When I started working in the embedded computer market in 2004, except for a few select customers in the defense sector of the industry, it was absolutely oblivious to security vulnerabilities. The ever increasing importance of connected systems and the emergence of the Internet of Things in recent years, however, have helped nurture an awareness for these concerns. Recognizing the need to protect the algorithms which control connected devices and also the necessity to safeguard the data generated and exchanged by them is one important step, but no trivial task whatsoever.
Safeguarding Connected Systems – No Trivial Task
The main challenge for embedded systems manufacturers like us at Kontron is that securing a computing platform is in essence a very individual endeavor. You first need to study the system and applications that need hardening, then assess attack vectors and threat levels on a case-by-case basis to prevent breaches. This, of course, while constantly struggling to keep the cost down for your customers and thus deter attackers in the most efficient way possible. This very complex and time-consuming approach to security itself is hardly efficient at all.

Safeguarding connected systems is the silver bullet (Quelle: www.pixabay.com).
Breaking it Down in Sellable Boxes
So we as a manufacturer are in essence faced with a challenge to break down this process into sellable boxes that, combined in the right way, suit every need. Customers would then no longer need to invest substantial sums into a gray area full of very individual threat scenarios, but rather profit from a cost-efficient one-size-fits-all solution. This in return would free up funds and open up ways for new revenue streams and new business models on their part. This is exactly what our new Kontron Security Solutions product line is all about.
Getting to the Bottom of Embedded Systems Security
Embedded systems security is always based on a chain of secure elements sitting on top of each other. Usually the foundation of this metaphorical pile of secure elements is a Trusted Platform Module (TPM), a dedicated microcontroller designed to secure hardware by integrating cryptographic keys into the device. For our new Kontron Security Solutions line we decided to build on this foundation. We developed an additional security chip that makes security easy to apply in order to simplify the process of hardening our devices. Why did we do that instead of utilizing the capabilities of the TPM which is there in the first place?
The TPM sits on the very bottom of things. Its primary objective is to safeguard the secure or trusted boot mechanism. From years of experience working closely with both Kontron customers and partners alike, I can confidently attest that few clients wish, let alone need to fortify their devices on this level. Their primary concern is much rather to protect as securely as possible their intellectual property, the application data stored on the device.
Kontron Approtect
This is where our first Kontron Security Solution, Kontron Approtect, comes into play. Instead of securing the very lowest boot level, like TPM does, we encrypt application binaries in a way that prevents reverse engineering. We add a control mechanism into our very own security chip that checks the application’s encryption. This ensures that only dedicated devices are able to run that application. Through this interaction with our security chip, which decrypts parts of the application while it is running, we ensure that the application cannot be easily dumped out of memory. The beauty of this solution is its simplicity. We do not need to invest into a trusted boot mechanism, boot attestation or infrastructure, which makes our concept very easy to apply.
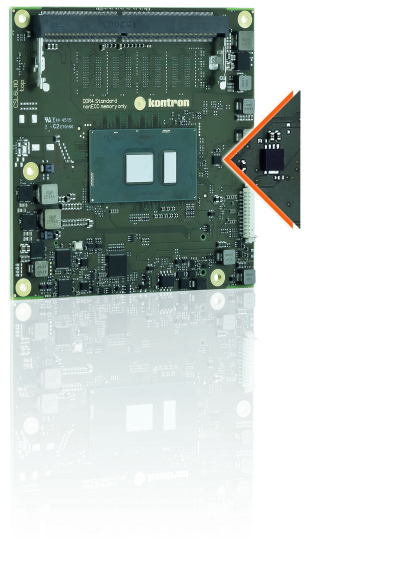
The COMe-bSL6 is provisioned with a security chip to enable the support of Kontron’s Embedded Security Solution.
Kontron Approtect secures applications without additional compiling effort or complex key handling processes. Here is how it works: A customer sends us the binary file that needs protecting. We quickly encrypt it and send it back to them alongside detailed configuration information that enable all desired devices to run and execute that binary. This is even possible for older existing binaries which have not been secured before. We offer this as a service. This drastically reduces the cost for our customers as they only pay for what they truly need.
Kontron Security Solutions: A Lot More to Come
While Kontron Approtect is the first product in our Security Solutions line, there are a lot more to come. We will be offering them alongside our secure trusted boot-solution as a standard option for every system. Further Kontron Security Solutions can help establish and enforce new business models. They could be used to enable certain application features for a specific amount of time or uses in trial scenarios for example.
As you can see, Kontron Security Solutions will open up an exciting new range of possibilities, stay tuned for more.

{{comment.comment}}